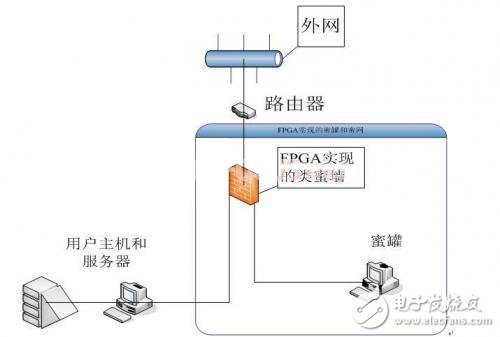
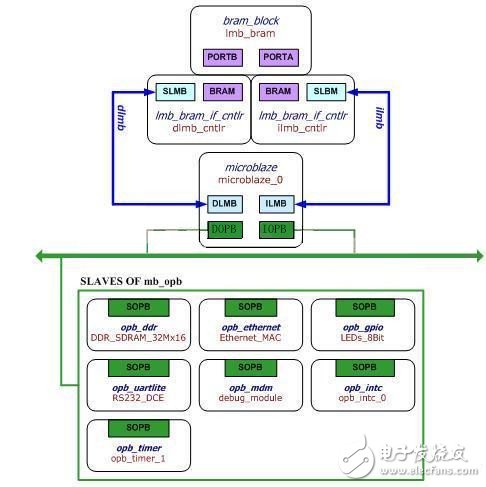
Project background Honeypot technology has been around for a long time, and Honeypot is a computer system that runs on the Internet. It is designed to attract and trick people who try to break into someone else's computer system (such as computer hackers), a vulnerability-based scam system that simulates one or more vulnerable hosts. Give the attacker a target that is easy to attack. Since honeypots do not provide truly valuable services to the outside world, all attempts to honeypots are considered suspicious. Another use of honeypots is to delay the attacker's attack on the real target, allowing the attacker to waste time on the honeypot. To put it simply: honeypots are a trap to trap an attacker. According to the interaction between the honeypot and the attacker, it can be divided into three categories: low-interaction honeypot, medium-interaction honeypot and high-interaction honeypot. At present, honeypots on the market are realized by software. Software has its weaknesses such as slow speed, strong dependence, and complicated procedures. Based on honeypots, it requires a large amount of data matching (intrusion auditing, etc.) and a secure system (simple). We think that honeypot technology can be realized with hardware FPGA. At present, the implementation of honeypot technology in hardware has never appeared in the network and related books and magazines. 2. Project objectives As the experiment we did with XILINUX's SPARTEN-3E experimental board, we wrote our own operating system and kernel based on the basic low-interaction honeypot, and achieved a highly interactive honeypot system. 3. The main content of the project This project is divided into three parts. a. Honey wall setting Features: Using FPGA to implement IDS and intrusion detection and intrusion auditing functions Prevent hackers from using honeypots as springboard attack servers b. Honeypot construction Features: Simulate a real operating system with FPGA Use the operating system to build a highly interactive honeypot on the FPGA experiment board for hackers c. Data collection and analysis Features: Transfer the effective data on the honeypot safely to other places Research and analyze the attack behavior of hackers or Trojans 4. Discussion on key technologies and innovation points of the project Key technologies include: IDS intrusion detection, intrusion auditing, honeypot technology and related logging analysis, honeynet and honeywall capabilities. At present, there is no FPGA or related hardware platform to implement honeypots and honeywalls in China. All honeypot technologies are based on software platforms. At the same time, the terminal security protection of the FPGA has been in a passive protection state. If the honeypot technology can be used, the terminal protection can be changed from passive to active, and the security of the terminal can be effectively and safely added. 5. Project achievements We finally completed the functional realization of the main work of the project, and tested the system composed of the honeypot honey wall with different attack methods. The test results show that the system we realized with FPGA can achieve the desired goal. 1. Implementing the honey wall technology using FPGA, which almost includes the intrusion detection of all attack modes in the current terminal attack. 2. Use the honey wall to induce the attack onto the honeypot implemented by the FPGA. 3. Realize the log record, detect and analyze the characteristics and methods of the attack, to further understand the attack and win the initiative for the future defense. Demand analysis and project objectives 1.1 Demand Analysis The three processes of honeypot development: The biggest feature of low-interaction honeypots is simulation. All the vulnerability and attack objects that honeypots show to attackers are not real product systems, but simulations of various systems and the services they provide. Because its services are simulated behaviors, honeypots have very limited information and can only respond to attackers simply. It is the safest type of honeypot. The middle interaction is a simulation of the various behaviors of the real operating system. It provides more interactive information and can also get more information from the attacker's behavior. In this simulated behavioral system, the honeypot can look no different from a real operating system. They are the target of the real system to be attractive. The high-interaction honeypot has a real operating system. Its advantage lies in providing the real system to the attacker. When the attacker gains ROOT permission, he is confused by the system and the authenticity of the data. His more activities and behaviors will be record it. The disadvantage is that the possibility of being invaded is very high. If the entire high honeypot is invaded, it will become a springboard for the attacker's next attack. However, if we have a honey wall to effectively prevent hackers from using honeypots as springboards, then we can solve the shortcomings of high-interaction honeypots and make honeypots truly a safe trap that we can control. And we use hardware to implement honeypot technology, which is hundreds of times faster than software. The real-time operating system can be installed on the FPGA, and the hardware is simpler and more basic than the software, and the protection effect is better. 1.2 achieved functional goals Realize high-interaction honeypot technology with FPGA and realize honey wall function, realize the underlying programming of hardware 1.3 Project feasibility analysis Because the hardware implementation of honeypot technology has not appeared in the current world, at least on the Chinese website, it is the first one. Many technical problems, especially software-to-hardware programming and implementation, are the main problems we face, but the hardware is fast. The structure is simple and the real-time performance is good. We can make full use of the honeypot and the honey wall to realize our hardware honeypot. The advantage realized by software is very obvious. Overall design of the project 2.1 Overall structure The above is our general system architecture diagram. We can see that Ethernet is equivalent to the external network through the router first through the honey wall we implemented with FPGA. He has many functions such as IDS, intrusion detection, intrusion auditing, etc. Most importantly, the highly interactive honeypot is easily attacked by hackers as a springboard for attacking the main server, but the honey wall can be well prevented. From the honeypot to the server attack, in short, he is a firewall that can't be accessed only for honeypots. After the data stream passes through the honey wall, we analyze the data. When no attack information is found, the data stream is sent to the server as normal data through the honey wall. If we detect the intrusion attack, the honey wall will use IP spoofing technology. The data stream of the attack is directed to the honeypot, so that the hacker can only attack the honeypot and not reach the real server. On the honeypot, we conduct real-time monitoring. The hacker's every move is under our surveillance. The information on the honeypot is exported through a safe way. We can analyze this information to understand and master the behavior of the hacker. To proactively defend against other attacks in the future. FPGA hardware implements operating system kernel with network connection 3.1 Basic structure and configuration of system hardware The hardware design of the system is configured using the Base System Builder in the Xilinx Platform Studio integrated development environment. The system block diagram of the completed design is shown in Figure XX. System hardware block diagram The core of the entire system hardware is the Microblaze processor. The basic configuration and main peripherals of the processor include: 3.2 Hardware Functions and Indicators First, the Microblaze processor: Processor bus frequency: 66.7 MHz; On-chip memory (BRAM): 16KB; Due to the limited BRAM resources of the Spartan-3e XC3S500E, the Cache function is not selected. Second, the basic peripheral configuration: (1) Serial port: RS232_DCE Baud rate: 115200, use interrupt; (2) Ethernet MAC: Using Xilinx Ethernet_MAC IP, its configuration parameters are: No DMA, use interrupt, and select FIFO mode to meet the needs of socket programming using lwIP under Xilkernel system; (3) Timer: Use a 32-bit timer and use an interrupt. (4) DDR_SRAM: Use 32Mx16 memory on the development board and configure it as OPB DDR. In addition, the system hardware includes: an interrupt controller, eight LEDs connected to the general purpose I/O, and a debug module. For more detailed hardware platform details, refer to the system's hardware description file (MHS). Copper Tube Terminals Without Checking Hole Our company specializes in the production and sales of all kinds of terminals, copper terminals, nose wire ears, cold pressed terminals, copper joints, but also according to customer requirements for customization and production, our raw materials are produced and sold by ourselves, we have their own raw materials processing plant, high purity T2 copper, quality and quantity, come to me to order it! Copper Tube Terminals Without Checking Hole,Cable Lugs Insulating Crimp Terminal,Cable Connector Tinned Copper Ring Terminal,Tubular Cable Lugs Crimp Terminal Taixing Longyi Terminals Co.,Ltd. , https://www.txlyterminals.com